SC-100 Exam Questions - Online Test
SC-100 Premium VCE File

150 Lectures, 20 Hours

High value of SC-100 practice exam materials and braindump for Microsoft certification for IT professionals, Real Success Guaranteed with Updated SC-100 pdf dumps vce Materials. 100% PASS Microsoft Cybersecurity Architect exam Today!
Also have SC-100 free dumps questions for you:
NEW QUESTION 1
Your on-premises network contains an e-commerce web app that was developed in Angular and Node.js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model. Solution: You recommend implementing Azure Front Door with Azure Web Application Firewall (WAF). Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 2
Your company plans to provision blob storage by using an Azure Storage account The blob storage will be accessible from 20 application sewers on the internet. You need to recommend a solution to ensure that only the application servers can access the storage account. What should you recommend using to secure the blob storage?
- A. service tags in network security groups (NSGs)
- B. managed rule sets in Azure Web Application Firewall (WAF) policies
- C. inbound rules in network security groups (NSGs)
- D. firewall rules for the storage account
- E. inbound rules in Azure Firewall
Answer: C
NEW QUESTION 3
You are evaluating the security of ClaimsApp.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE; Each correct selection is worth one point.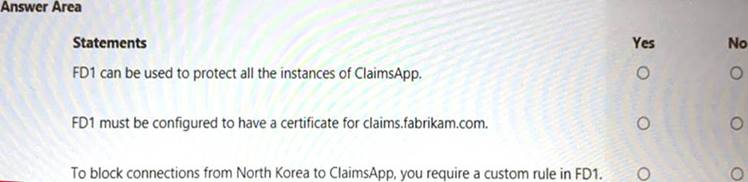
Solution:
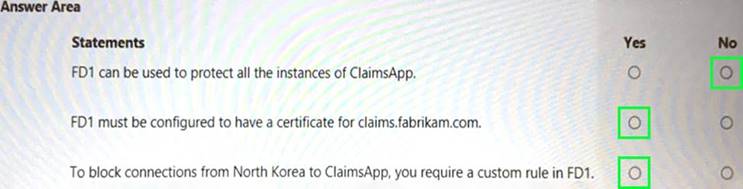
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 4
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling adaptive network hardening. Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 5
You have a Microsoft 365 E5 subscription.
You are designing a solution to protect confidential data in Microsoft SharePoint Online sites that contain more than one million documents.
You need to recommend a solution to prevent Personally Identifiable Information (Pll) from being shared.
Which two components should you include in the recommendation? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. data loss prevention (DLP) policies
- B. sensitivity label policies
- C. retention label policies
- D. eDiscovery cases
Answer: AD
NEW QUESTION 6
Your company has a third-party security information and event management (SIEM) solution that uses Splunk and Microsoft Sentinel. You plan to integrate Microsoft Sentinel with Splunk.
You need to recommend a solution to send security events from Microsoft Sentinel to Splunk. What should you include in the recommendation?
- A. Azure Event Hubs
- B. Azure Data Factor
- C. a Microsoft Sentinel workbook
- D. a Microsoft Sentinel data connector
Answer: C
NEW QUESTION 7
You are planning the security requirements for Azure Cosmos DB Core (SQL) API accounts. You need to recommend a solution to audit all users that access the data in the Azure Cosmos DB accounts. Which two configurations should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A. Enable Microsoft Defender for Cosmos DB.
- B. Send the Azure Active Directory (Azure AD) sign-in logs to a Log Analytics workspace.
- C. Disable local authentication for Azure Cosmos DB.
- D. Enable Microsoft Defender for Identity.
- E. Send the Azure Cosmos DB logs to a Log Analytics workspace.
Answer: AD
NEW QUESTION 8
You have an Azure subscription that has Microsoft Defender for Cloud enabled. Suspicious authentication activity alerts have been appearing in the Workload protections dashboard.
You need to recommend a solution to evaluate and remediate the alerts by using workflow automation. The solution must minimize development effort. What should you include in the recommendation?
- A. Azure Monitor webhooks
- B. Azure Logics Apps
- C. Azure Event Hubs
- D. Azure Functions apps
Answer: D
NEW QUESTION 9
You have a customer that has a Microsoft 365 subscription and an Azure subscription.
The customer has devices that run either Windows, iOS, Android, or macOS. The Windows devices are deployed on-premises and in Azure.
You need to design a security solution to assess whether all the devices meet the customer's compliance rules. What should you include in the solution?
- A. Microsoft Information Protection
- B. Microsoft Defender for Endpoint
- C. Microsoft Sentinel
- D. Microsoft Endpoint Manager
Answer: D
NEW QUESTION 10
Your company has a hybrid cloud infrastructure.
The company plans to hire several temporary employees within a brief period. The temporary employees will need to access applications and data on the company' premises network.
The company's security policy prevents the use of personal devices for accessing company data and applications.
You need to recommend a solution to provide the temporary employee with access to company resources. The solution must be able to scale on demand.
What should you include in the recommendation?
- A. Migrate the on-premises applications to cloud-based applications.
- B. Redesign the VPN infrastructure by adopting a split tunnel configuration.
- C. Deploy Microsoft Endpoint Manager and Azure Active Directory (Azure AD) Conditional Access.
- D. Deploy Azure Virtual Desktop, Azure Active Directory (Azure AD) Conditional Access, and Microsoft Defender for Cloud Apps.
Answer: D
NEW QUESTION 11
You have a customer that has a Microsoft 365 subscription and uses the Free edition of Azure Active Directory (Azure AD)
The customer plans to obtain an Azure subscription and provision several Azure resources. You need to evaluate the customer's security environment.
What will necessitate an upgrade from the Azure AD Free edition to the Premium edition?
- A. role-based authorization
- B. Azure AD Privileged Identity Management (PIM)
- C. resource-based authorization
- D. Azure AD Multi-Factor Authentication
Answer: A
NEW QUESTION 12
Your company is moving all on-premises workloads to Azure and Microsoft 365. Vou need to design a security orchestration, automation, and response (SOAR) strategy in Microsoft Sentinel that meets the following requirements:
• Minimizes manual intervention by security operation analysts
• Supports Waging alerts within Microsoft Teams channels What should you include in the strategy?
- A. data connectors
- B. playbooks
- C. workbooks
- D. KQL
Answer: C
NEW QUESTION 13
Your company is developing a serverless application in Azure that will have the architecture shown in the following exhibit.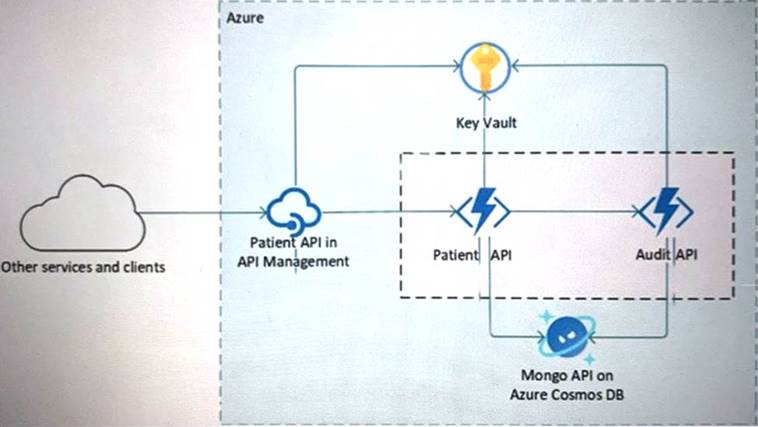
You need to recommend a solution to isolate the compute components on an Azure virtual network. What should you include in the recommendation?
- A. Azure Active Directory (Azure AD) enterprise applications
- B. an Azure App Service Environment (ASE)
- C. Azure service endpoints
- D. an Azure Active Directory (Azure AD) application proxy
Answer: B
NEW QUESTION 14
You are designing an auditing solution for Azure landing zones that will contain the following components:
• SQL audit logs for Azure SQL databases
• Windows Security logs from Azure virtual machines
• Azure App Service audit logs from App Service web apps
You need to recommend a centralized logging solution for the landing zones. The solution must meet the following requirements:
• Log all privileged access.
• Retain logs for at least 365 days.
• Minimize costs.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.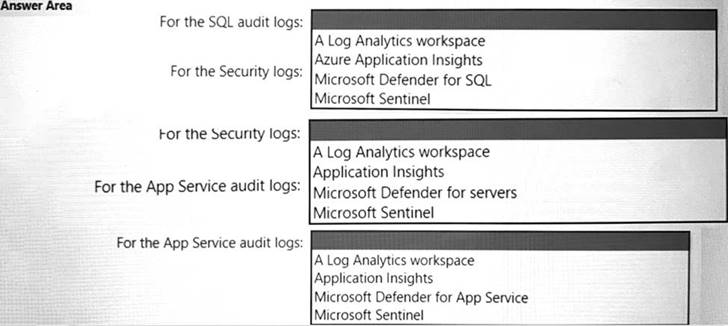
Solution:
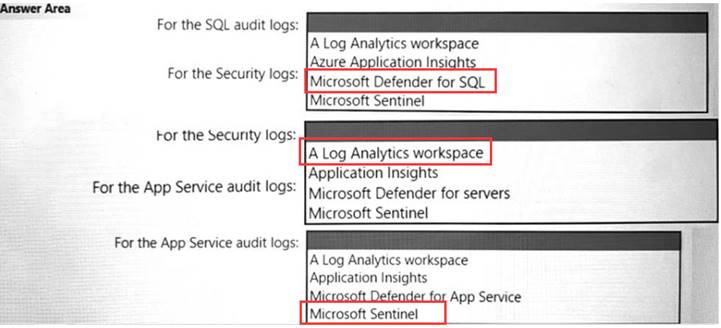
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 15
A customer follows the Zero Trust model and explicitly verifies each attempt to access its corporate applications.
The customer discovers that several endpoints are infected with malware. The customer suspends access attempts from the infected endpoints.
The malware is removed from the end point.
Which two conditions must be met before endpoint users can access the corporate applications again? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. Microsoft Defender for Endpoint reports the endpoints as compliant.
- B. Microsoft Intune reports the endpoints as compliant.
- C. A new Azure Active Directory (Azure AD) Conditional Access policy is enforced.
- D. The client access tokens are refreshed.
Answer: CD
NEW QUESTION 16
Your company has a Microsoft 365 E5 subscription.
The Chief Compliance Officer plans to enhance privacy management in the working environment. You need to recommend a solution to enhance the privacy management. The solution must meet the following requirements:
• Identify unused personal data and empower users to make smart data handling decisions.
• Provide users with notifications and guidance when a user sends personal data in Microsoft Teams.
• Provide users with recommendations to mitigate privacy risks. What should you include in the recommendation?
- A. Microsoft Viva Insights
- B. Advanced eDiscovery
- C. Privacy Risk Management in Microsoft Priva
- D. communication compliance in insider risk management
Answer: A
NEW QUESTION 17
Your company has a hybrid cloud infrastructure.
Data and applications are moved regularly between cloud environments.
The company's on-premises network is managed as shown in the following exhibit.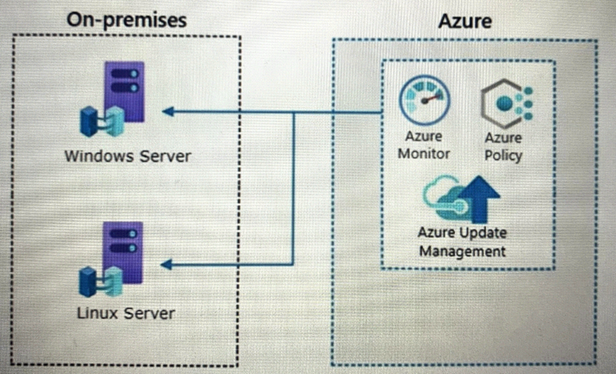
NOTE Each correct selection is worth one point.
- A. Azure VPN Gateway
- B. guest configuration in Azure Policy
- C. on-premises data gateway
- D. Azure Bastion
- E. Azure Arc
Answer: CE
NEW QUESTION 18
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points.
You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling just-in-time (JIT) VM access on all virtual machines.
Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 19
You are designing security for a runbook in an Azure Automation account. The runbook will copy data to Azure Data Lake Storage Gen2.
You need to recommend a solution to secure the components of the copy process.
What should you include in the recommendation for each component? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.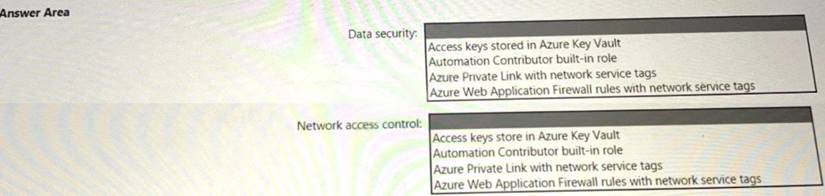
Solution:
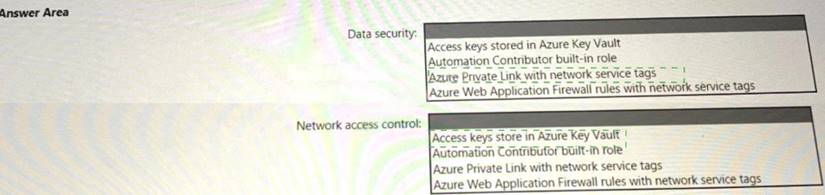
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 20
......
P.S. Easily pass SC-100 Exam with 105 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader SC-100 Dumps: https://www.certleader.com/SC-100-dumps.html (105 New Questions)
- [2021-New] Microsoft 70-461 Dumps With Update Exam Questions (41-50)
- Printable DP-200 Q&A 2021
- [2021-New] Microsoft 70-499 Dumps With Update Exam Questions (31-40)
- [2021-New] Microsoft 70-410 Dumps With Update Exam Questions (51-60)
- [2021-New] Microsoft 70-410 Dumps With Update Exam Questions (121-130)
- [2021-New] Microsoft 70-980 Dumps With Update Exam Questions (121-130)
- [2021-New] Microsoft 70-413 Dumps With Update Exam Questions (71-80)
- [2021-New] Microsoft 70-462 Dumps With Update Exam Questions (61-70)
- [2021-New] Microsoft 70-463 Dumps With Update Exam Questions (121-130)
- [2021-New] Microsoft 70-499 Dumps With Update Exam Questions (91-100)

