70-398 Exam Questions - Online Test
70-398 Premium VCE File

150 Lectures, 20 Hours

It is impossible to pass Microsoft 70-398 exam without any help in the short term. Come to us soon and find the most advanced, correct and guaranteed . You will get a surprising result by our .
Microsoft 70-398 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
A Sales department user overwrites a version of a Word document on their device.
You need to view the events that you monitored for Marketing users. Which log file should you view?
- A. StatusAgent Log
- B. System Event Log
- C. Security Event Log
- D. PolicyAgent Log
- E. Application Event Log
Answer: C
Explanation: References:
https://docs.microsoft.com/en-us/windows/device-security/auditing/view-the-security-event- log
NEW QUESTION 2
DRAG DROP
Your organization needs to implement a Dynamic Access Control (DAC) plan that includes user and device claims.
The domain controllers have not been enabled to provide claims and compound authentication.
You need to configure the Default Domain Controller’s Group Policy Object to provide claims and compound authentication.
You decide to first enable the domain controllers to provide claims and compound authentication on request.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.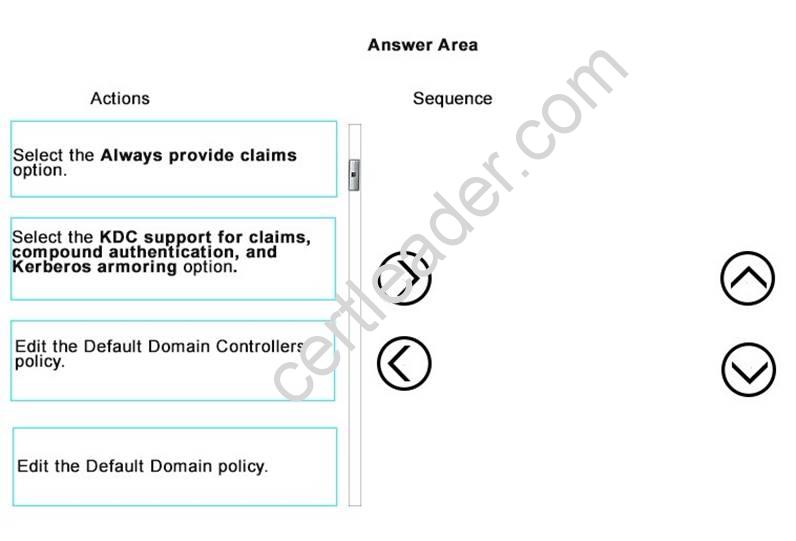
Answer:
Explanation: 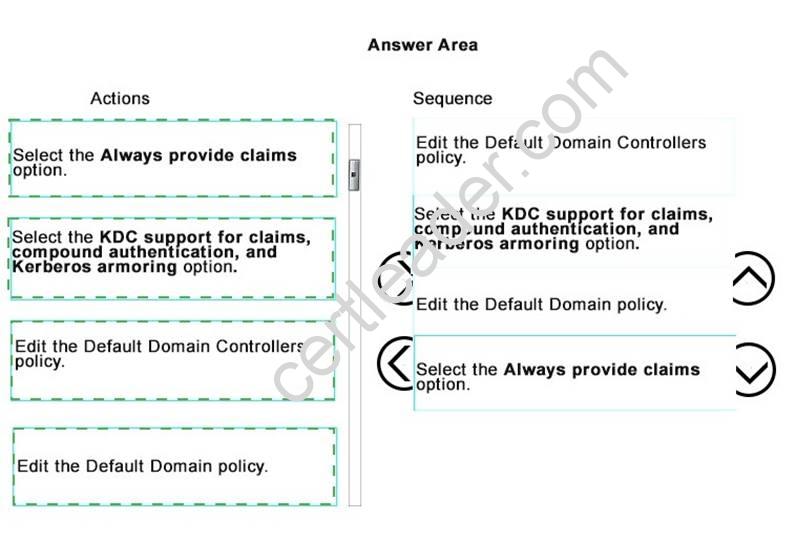
NEW QUESTION 3
A company deploys Outlook to all users that have iOS and Android devices. The company uses Microsoft Intune to manage mobile devices. You enforce a conditional access policy that requires users to enroll devices in Intune before they can access Exchange ActiveSync data.
Some Android and iOS users access Exchange ActiveSync data by using unmanaged email applications.
You need to ensure that users Exchange ActiveSync data only from Outlook. What should you do?
- A. Create an Exchange access rul
- B. Select Outlook family and Outlook for Android and iOS as the model.
- C. In Intune, create a new compliance policy that forces email accounts to be managed by Intune.
- D. Create a security group for all users that are not using Outlook as the email application
- E. Configure Exchange Online conditional access policy to exempt members of the group.
- F. Configure a custom Open Mobile Alliance Uniform Resource Identifier setting and deploy the setting to all users.
Answer: A
NEW QUESTION 4
You are a network administrator for a company that has an Office 365 E3 subscription. You purchase Enterprise Mobility Suite licenses. You implement synchronization by using a federated identity model.
Passwords for Sales team users often expire while they are travelling. When this happens, the users are not able to log on to the virtual private network (VPN) to perform their duties. Users must be able to reset their own passwords.
You need to enable password write-back. Which application should you configure?
- A. Web Application Proxy
- B. Active Directory Federation Services (AD FS)
- C. Microsoft Online Services Sign-in Assistant
- D. Directory Synchronization (DirSync)
- E. Azure Active Directory Connect
Answer: E
NEW QUESTION 5
A Sales department user overwrites a version of a Word document on their device. You need to configure access for the contractors.
Which two actions should you perform? Each correct answer presents part of the solution.
- A. Store the BitLocker recovery keys in the contoso.com domain.
- B. Create a Microsoft account for each contractor.
- C. Store the BitLocker recovery keys inOneDrive.
- D. Join the contractors’ devices to the contoso.com Active Directory Domain Services (AD DS) domain.
- E. Create Active Directory Domain Services (AD DS) domain user accounts for each contractor.
Answer: BC
NEW QUESTION 6
DRAG DROP
You have a computer that runs Windows 10 Enterprise that contains the following folders: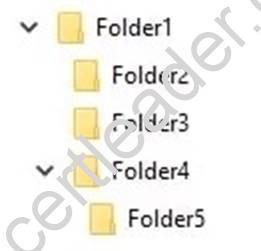
You have a local user named User1. User1 has read and execute permission to Folder1. You need to ensure that User1 can perform the following tasks:
The solution must use the principle of least privilege.
Which permissions should you assign to User1 on each folder? To answer, drag the appropriate permissions to the correct folders. Each permission may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Answer:
Explanation: Advanced permissions are detailed permissions that are grouped together to create the standard permissions. The permissions in this question are standard permissions.
Folder2: To create new files in a folder, you need Write permission to the folder. The ‘Write’ standard permission includes the ‘Create files / write data’ advanced permission.
Folder3: To edit existing files in a folder, you need Modify permission.
Folder5: To change the permissions of files in a folder, you need the ‘Change Permissions’ advanced permission. The Change Permission advanced permission is in the ‘Full Control’ standard permission group. Therefore, the answer for Folder5 is Full Control.
References: http://windows.microsoft.com/en-gb/windows/before-applying-permissions-file-folder#1TC=windows-7
NEW QUESTION 7
You manage an Active Directory Domain Services (AD DS) domain that has 500 devices. All devices run Windows 7 Enterprise Edition. You deploy System Center 2012 R2 Configuration Manager SP1.
You plan to upgrade all devices to Windows 10 Enterprise and encrypt the devices by using Microsoft BitLocker Administration and Monitoring (MBAM), Data secured with BitLocker must not be stored on USB devices.
You need to ensure that existing devices are ready for the upgrade. What should you do?
- A. Implement MBAM in thedomai
- B. Create an MBAM group policy and apply the policy to all devices.
- C. Verify that the System Center Configuration Manager agent is installed on all devices.
- D. In the system BIOS, verify that all devices have a Trusted Platform Module (TPM) 1.2 orhigher chi
- E. Enable the TPM chip.
- F. Integrate MBAM with System Center Configuration Manage
- G. Deploy the BitLocker prepare task sequence to all laptop computers.
- H. From System Center Configuration Manager, create a custom deploy task sequence that enables MBA
- I. Deploy the task sequence to all Windows 7 devices.
Answer: B
NEW QUESTION 8
DRAG DROP
Your organization is deploying new Windows 10 devices. You create a new organizational unit that contains all Windows 10 devices.
You are preparing a new security policy for Windows 10 devices. Your organization requires audits on the use of removable storage devices on personal devices.
You need to enable audits of removable storage.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.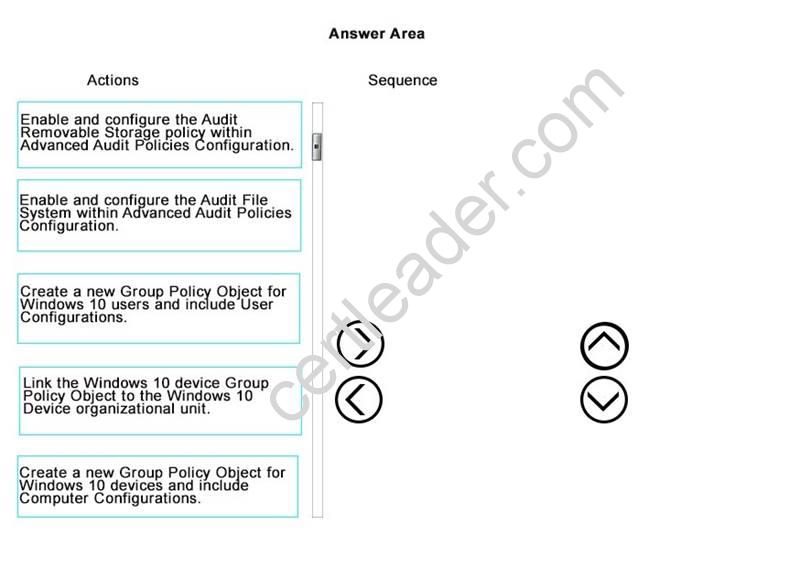
Answer:
Explanation: 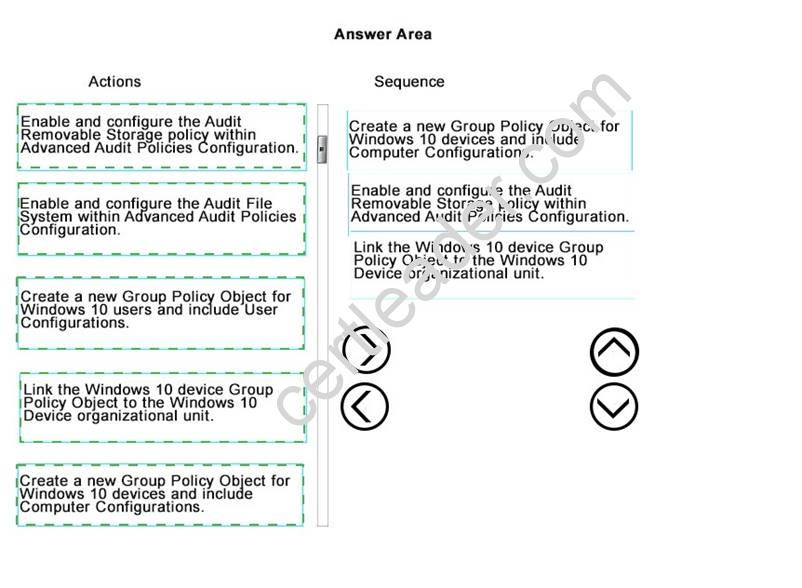
NEW QUESTION 9
DRAG DROP
A company uses Office 365 for email and instant messaging. You deploy Azure Active Directory (AD) Connect and enable password synchronization. The company acquires Enterprise Mobility Suite licenses.
You must allow users to update their passwords online. You need to configure Azure AD Connect.
Which three actions should you perform in sequence? To answer, move the appropriate
actions from the list of actions to the answer area and arrange them in the correct order.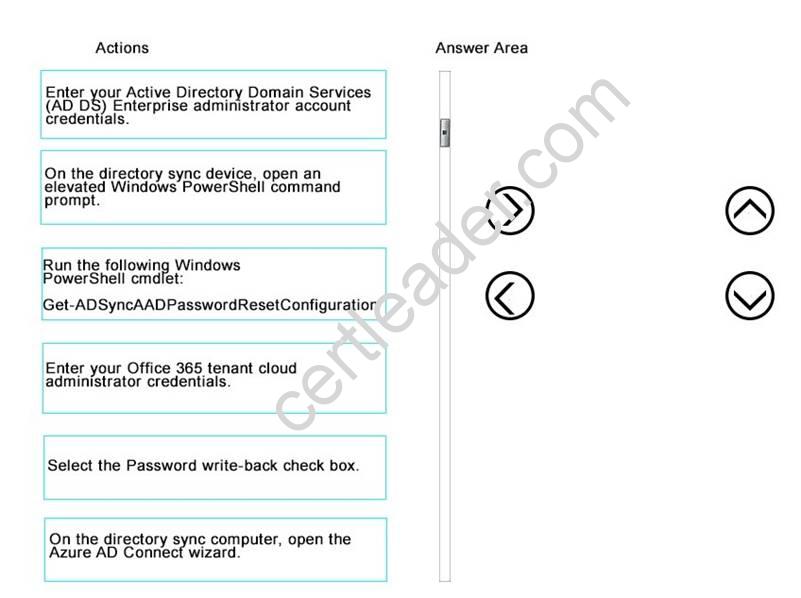
Answer:
Explanation: 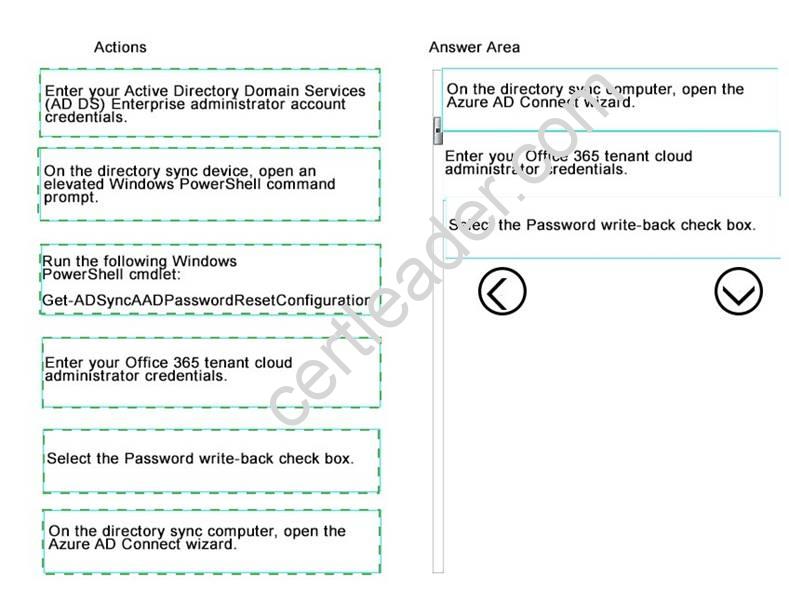
NEW QUESTION 10
You administer a Windows 10 Enterprise computer. The computer has File History turned on, and system protection turned on for drive C.
You accidentally delete a folder named LibrariesCustomers by using the Shift+Delete keyboard shortcut.
You need to restore the most recent version of the folder to its original location. Which approach should you use to restore the folder?
- A. Recycle Bin
- B. the latest restore point
- C. File History
- D. a manually selected restore point
Answer: C
Explanation: File History is similar to Previous Versions in previous versions of Windows. It takes regular backups of your data and saves them to a separate disk volume or external drive. When File History is enabled, it backs up all the system libraries and your custom libraries by default.
To restore a deleted folder, you can browse to the parent folder or library and select Restore Previous Versions. The Previous Versions tab will list the previous versions that can be restored to its original location or restored to an alternative location.
NEW QUESTION 11
HOTSPOT
You have a server that runs Windows Server 2012 R2 server named Server1. Server1 has Remote Desktop Services (RDS) installed. You create a session collection named Session1 and publish a RemoteApp in Session1.
Server1 has an application named App1. The executable for App1 is C:AppsApp1.exe.
You need to ensure that App1 is available as a RemoteApp in Session1.
What command should you run? To answer, select the appropriate options in the answer area.
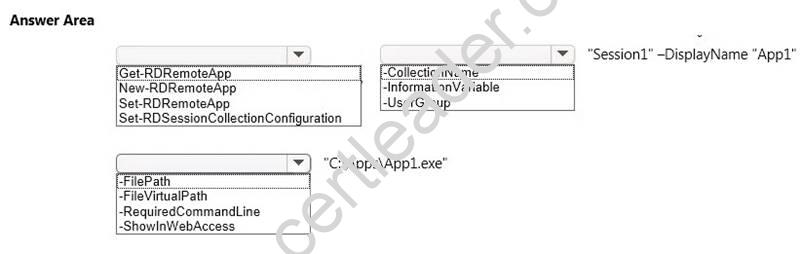
Answer:
Explanation: We need to publish App1 as a RemoteApp. We do this with the New–RDRemoteApp cmdlet.
The –CollectionName parameter allows us to specify the session as “Session1”. The display name for the App1 will be “App1”.
The –FilePath parameter allows us to specify the path to the executable for App1.
NEW QUESTION 12
HOTSPOT
You have a standalone computer that runs Windows 10 Enterprise. The computer is configured to automatically back up files by using File History. The user of the computer uses the OneDrive desktop app to sync files.
The Previous Versions settings from the local group policy of the computer are shown in the following graphic.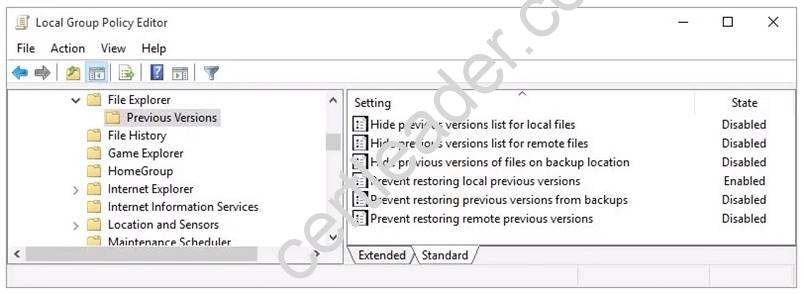
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
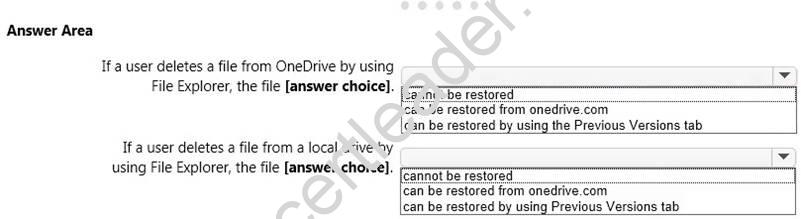
NOTE: Each correct selection is worth one point.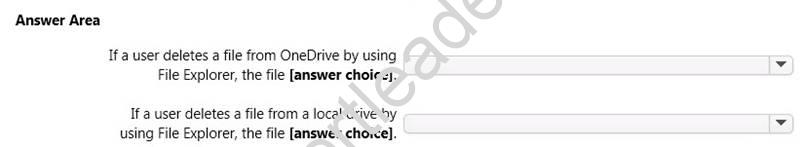
Answer:
Explanation: When a file is deleted from the local OneDrive folder with File Explorer, the deletion is replicated to Onedrive.com and the file is moved to the OneDrive recycle bin. The deleted file can therefore be recovered from the Recycle Binon Onedrive.com.
If a user deletes a file from a local drive by using File Explorer, the file cannot be restored. If the file is not in the OneDrive folder, it will not be a file that is synced to onedrive.com. We could use Previous Versions to restore the file but this is prevented by the Group Policy settings. The “Prevent restoring local previous versions” – Enabled group policy setting would prevent the previous version from being restored.
References: http://www.groovypost.com/howto/restore-deleted-files-local-onedrive-folder/
NEW QUESTION 13
You use a Windows 8.1 tablet. The tablet receives Windows Update updates automatically from the Internet.
The tablet has Wi-Fi and is connected to a 3G mobile broadband Wi-Fi hot spot. You need to minimize data usage while connected to this hot spot.
What should you do?
- A. Turn on Airplane Mode.
- B. Disable File and Print Sharing for mobile broadband connections.
- C. Configure the interface metric of IP settings for Wi-Fi connection as1.
- D. Edit the Inbound Rule of Windows Firewall, and then disable Internet Control Message Protocol (ICMP) traffic.
- E. Configure the broadband connection as a metered network.
Answer: E
Explanation: You can limit the bandwidth used by the broadband connection by configuring it as a metered network. A metered network is a network where data downloaded is ‘metered’(measured) and you are charged for the amount of data downloaded.
Setting a connection as metered prevents Windows from automatically using bandwidth in a number of ways including the following:
Disables automatic downloading of Windows updates: Windows won’t automatically download updates from Windows Update on metered Internet connections. You’ll get a “Download” button you can click whenever you want to install updates.
Disables automatic downloading of app updates: The Windows Store won’t automatically download updates for your installed “Store apps” on metered connections, either. Desktop apps like Chrome, Firefox, and others will continue updating themselves normally.
Tiles may not update: Microsoft says that the live tiles on your Start menu or Start screen “may” stop updating on a metered connection:
NEW QUESTION 14
HOTSPOT
A company has a Remote Desktop (RD) Services farm. The farm has six servers that run Windows Server 2008, five RD Session Host servers, and one RD Connection Broker server. User RD profiles are redirected to a hidden folder named PROFILES on a file server named FILTER01.
You must provide a deployment plan for migrating the RD farm to Windows Server 2012 R2. The new farm must use the same file server share to redirect user RD profiles. Users must be able to log on to any server and have the same experience.
You need to configure RD Services.
What should you do? To answer, select the appropriate action from each list in the answer area.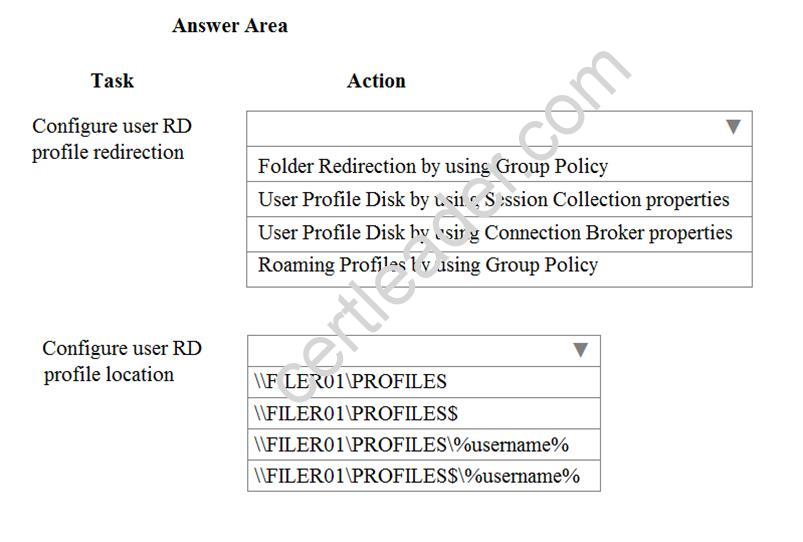
Answer:
Explanation: References:
http://woshub.com/user-profile-disks-in-windows-server-2012-r2-rds/
NEW QUESTION 15
You have a Windows 10 Enterprise computer named Computer1. Computer1 has File History enabled.
You create a folder named Folder1 in the root of the C: drive. You need to ensure that Folder1 is protected by File History.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
- A. From File Explorer, include Folder1 in an existing library.
- B. Modify the Advanced settings from the FileHistory Control Panel item.
- C. From the Settings app, modify the Backup options.
- D. From File Explorer, modify the system attribute of Folder1.
Answer: AC
Explanation: By default, File History backs up all libraries. We can therefore ensure that Folder1 is protected by File History by adding the folder to a library.
The second method of ensuring that Folder1 is protected by File History is to add the folder location to File History. You do this by modifying the Backup options, not the File History Control Panel item as you might expect. In the Settings app, select Update & Security then Backup. Under the Back up using File History heading, select the Add a drive option.
NEW QUESTION 16
HOTSPOT
Your company upgrades a research and development department workstation to a Windows 10 Enterprise computer. Two of the workstation’s folders need to be encrypted. The folders are named C:ProtectedFiles and C:Backups.
You attempt to encrypt the folders. The output is shown in the following exhibit.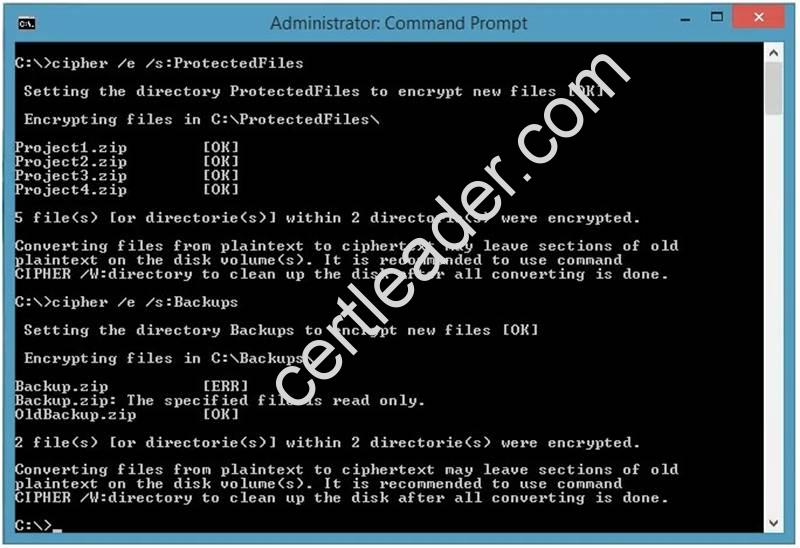
Use the drop-down menus to select the answer choice that completes each statement. NOTE: Each correct selection is worth one point.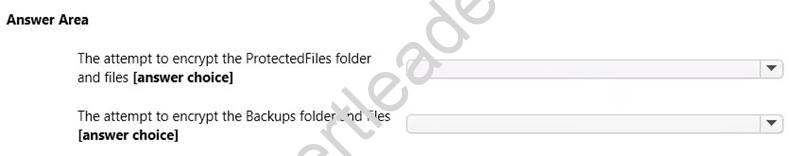
Answer:
Explanation: We can see from the image below that all files and the ProtectedFiles folder were encrypted successfully (There are no errors and there is an [OK] message for each action).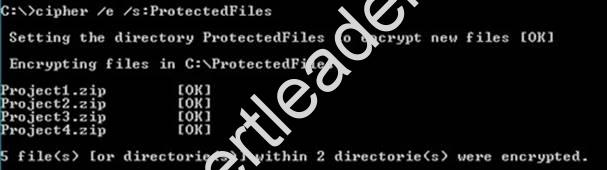
The image below shows that the folder was encrypted successfully (Setting the directory Backups to encrypt new files [OK]).
The file Backup.zip failed to encrypt because the file is read only. The other file, OldBackup.zip was encrypted successfully.
References: https://technet.microsoft.com/en-us/library/bb490878.aspx
NEW QUESTION 17
DRAG DROP
You need to resolve the Security team service announcement.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.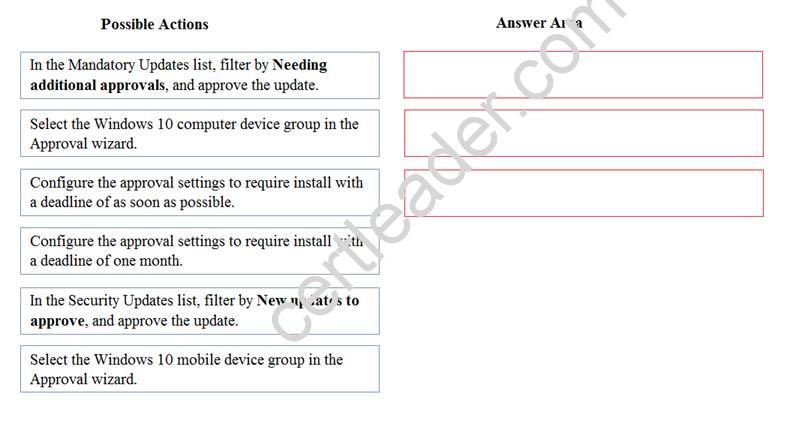
Answer:
Explanation: 1: In the Mandatory Updates list, filter by Needing additional approvals, and approve the update.
2: Select the Windows 10 computer device group in the Approval wizard.
3: Configure the approval settings to require install with a deadline as soon as possible.
References:
https://www.credera.com/blog/infrastructure/understanding-windows-updates-for-pcs-with-microsoft-intune/
100% Valid and Newest Version 70-398 Questions & Answers shared by 2passeasy, Get Full Dumps HERE: https://www.2passeasy.com/dumps/70-398/ (New 74 Q&As)
- [2021-New] Microsoft 98-375 Dumps With Update Exam Questions (1-10)
- [2021-New] Microsoft 70-487 Dumps With Update Exam Questions (61-67)
- [2021-New] Microsoft 70-383 Dumps With Update Exam Questions (151-160)
- How Many Questions Of MB-901 Study Guide
- Microsoft 70-348 Forum 2021
- [2021-New] Microsoft 70-981 Dumps With Update Exam Questions (91-100)
- [2021-New] Microsoft 70-696 Dumps With Update Exam Questions (1-10)
- Up To Date 98-349 Testing Engine 2021
- Vivid MB2-715 Braindumps 2021
- How Many Questions Of 70-745 Testing Software

