156-215.80 Exam Questions - Online Test
156-215.80 Premium VCE File

150 Lectures, 20 Hours

It is impossible to pass Check-Point 156-215.80 exam without any help in the short term. Come to Examcollection soon and find the most advanced, correct and guaranteed Check-Point 156-215.80 practice questions. You will get a surprising result by our Avant-garde Check Point Certified Security Administrator practice guides.
Free 156-215.80 Demo Online For Check-Point Certifitcation:
NEW QUESTION 1
What key is used to save the current CPView page in a filename format cpview_"cpview process ID".cap"number of captures"?
- A. S
- B. W
- C. C
- D. Space bar
Answer: B
NEW QUESTION 2
Review the following screenshot and select the BEST answer.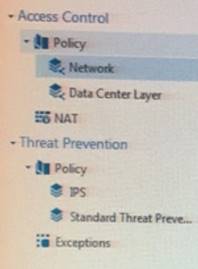
- A. Data Center Layer is an inline layer in the Access Control Policy.
- B. By default all layers are shared with all policies.
- C. If a connection is dropped in Network Layer, it will not be matched against the rules in Data Center Layer.
- D. If a connection is accepted in Network-layer, it will not be matched against the rules in Data Center Layer.
Answer: C
NEW QUESTION 3
Jennifer McHanry is CEO of ACME. She recently bought her own personal iPad. She wants use her iPad to access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the R77 Firewall Rule Base.
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network destinations. Select accept as the Action.
4) Install policy.
Ms McHanry tries to access the resource but is unable. What should she do?
- A. Have the security administrator select the Action field of the Firewall Rule “Redirect HTTP connections to an authentication (captive) portal”.
- B. Have the security administrator reboot the firewall.
- C. Have the security administrator select Any for the Machines tab in the appropriate Access Role.
- D. Install the Identity Awareness agent on her iPad.
Answer: A
NEW QUESTION 4
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
- A. UserCheck
- B. Active Directory Query
- C. Account Unit Query
- D. User Directory Query
Answer: B
Explanation:
AD Query extracts user and computer identity information from the Active Directory Security Event Logs. The system generates a Security Event log entry when a user or computer accesses a network resource. For example, this occurs when a user logs in, unlocks a screen, or accesses a network drive.
Reference : https://sc1.checkpoint.com/documents/R76/CP_R76_IdentityAwareness_AdminGuide/62402.htm
NEW QUESTION 5
What is the BEST command to view configuration details of all interfaces in Gaia CLISH?
- A. ifconfig -a
- B. show interfaces
- C. show interfaces detail
- D. show configuration interface
Answer: D
NEW QUESTION 6
Fill the blank. IT is Best Practice to have a _____ rule at the end of each policy layer.
- A. Explicit Drop
- B. Implied Drop
- C. Explicit Cleanup
- D. Implicit Drop
Answer: A
NEW QUESTION 7
Joey wants to configure NTP on R80 Security Management Server. He decided to do this via WebUI. What is the correct address to access the Web UI for Gaia platform via browser?
- A. https://<Device_IP_Address>
- B. https://<Device_IP_Address>:443
- C. https://<Device_IP_Address>:10000
- D. https://<Device_IP_Address>:4434
Answer: A
Explanation:
Access to Web UI Gaia administration interface, initiate a connection from a browser to the default administration IP address: Logging in to the WebUI
Logging in
To log in to the WebUI:
Enter this URL in your browser: https://<Gaia IP address>
Enter your user name and password. References:
NEW QUESTION 8
You are conducting a security audit. While reviewing configuration files and logs, you notice logs accepting POP3 traffic, but you do not see a rule allowing POP3 traffic in the Rule Base. Which of the following is the
most likely cause?
- A. The POP3 rule is disabled.
- B. POP3 is accepted in Global Properties.
- C. The POP3 rule is hidden.
- D. POP3 is one of 3 services (POP3, IMAP, and SMTP) accepted by the default mail object in R77.
Answer: C
NEW QUESTION 9
Fill in the blanks: A Check Point software license consists of a _____ and ______.
- A. Software container; software package
- B. Software blade; software container
- C. Software package; signature
- D. Signature; software blade
Answer: B
Explanation:
Check Point's licensing is designed to be scalable and modular. To this end, Check Point offers both predefined packages as well as the ability to custom build a solution tailored to the needs of the Network Administrator. This is accomplished by the use of the following license components:
Software Blades
Container
NEW QUESTION 10
Choose the SmartLog property that is TRUE.
- A. SmartLog has been an option since release R71.10.
- B. SmartLog is not a Check Point product.
- C. SmartLog and SmartView Tracker are mutually exclusive.
- D. SmartLog is a client of SmartConsole that enables enterprises to centrally track log records and security activity with Google-like search.
Answer: D
NEW QUESTION 11
What are the three essential components of the Check Point Security Management Architecture?
- A. SmartConsole, Security Management Server, Security Gateway
- B. SmartConsole, SmartUpdate, Security Gateway
- C. Security Management Server, Security Gateway, Command Line Interface
- D. WebUI, SmartConsole, Security Gateway
Answer: A
Explanation:
Standalone deployment - Security Gateway and the Security Management server are installed on the same machine.
Distributed deployment - Security Gateway and the Security Management server are installed on different machines.
Deployments
Basic deployments: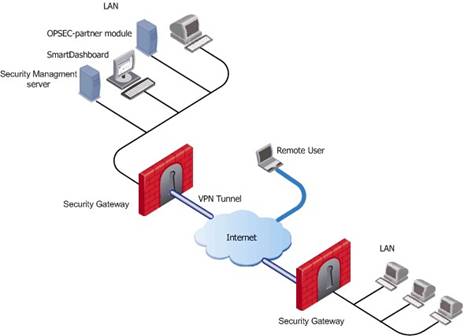
Assume an environment with gateways on different sites. Each Security Gateway connects to the Internet on one side, and to a LAN on the other.
You can create a Virtual Private Network (VPN) between the two Security Gateways, to secure all communication between them.
The Security Management server is installed in the LAN, and is protected by a Security Gateway. The Security Management server manages the Security Gateways and lets remote users connect securely to the corporate network. SmartDashboard can be installed on the Security Management server or another computer.
There can be other OPSEC-partner modules (for example, an Anti-Virus Server) to complete the network security with the Security Management server and its Security Gateways.
NEW QUESTION 12
The fw monitor utility is used to troubleshoot which of the following problems?
- A. Phase two key negotiation
- B. Address translation
- C. Log Consolidation Engine
- D. User data base corruption
Answer: B
NEW QUESTION 13
To optimize Rule Base efficiency, the most hit rules should be where?
- A. Removed from the Rule Base.
- B. Towards the middle of the Rule Base.
- C. Towards the top of the Rule Base.
- D. Towards the bottom of the Rule Base.
Answer: C
Explanation:
It is logical that if lesser rules are checked for the matched rule to be found the lesser CPU cycles the device is using. Checkpoint match a session from the first rule on top till the last on the bottom.
NEW QUESTION 14
Which of the following is NOT a VPN routing option available in a star community?
- A. To satellites through center only
- B. To center, or through the center to other satellites, to Internet and other VPN targets
- C. To center and to other satellites through center
- D. To center only
Answer: A
Explanation:
SmartConsole
For simple hubs and spokes (or if there is only one Hub), the easiest way is to configure a VPN star community in R80 SmartConsole:
On the Star Communitywindow, in the:
Center Gateways section, select the Security Gateway that functions as the "Hub".
Satellite Gateways section, select Security Gateways as the "spokes", or satellites.
On the VPN Routing page, Enable VPN routing for satellites section, select one of these options:
To center and to other Satellites through center - This allows connectivity between the Security Gateways, for example if the spoke Security Gateways are DAIP Security Gateways, and the Hub is a Security Gateway with a static IP address.
To center, or through the center to other satellites, to internet and other VPN targets - This allows connectivity between the Security Gateways as well as the ability to inspect all communication passing through the Hub to the Internet.
Create an appropriate Access Control Policy rule.
NAT the satellite Security Gateways on the Hub if the Hub is used to route connections from Satellites to the Internet.
The two Dynamic Objects (DAIP Security Gateways) can securely route communication through the Security Gateway with the static IP address.
NEW QUESTION 15
After the initial installation the First Time Configuration Wizard should be run. Select the BEST answer.
- A. First Time Configuration Wizard can be run from the Unified SmartConsole.
- B. First Time Configuration Wizard can be run from the command line or from the WebUI.
- C. First time Configuration Wizard can only be run from the WebUI.
- D. Connection to the internet is required before running the First Time Configuration wizard.
Answer: B
Explanation:
Check Point Security Gateway and Check Point Security Management require running the First Time Configuration Wizard in order to be configured correctly. The First Time Configuration Wizard is available in Gaia Portal and also through CLI.
To invoke the First Time Configuration Wizard through CLI, run the config_system command from the Exp shell.
NEW QUESTION 16
In the Check Point three-tiered architecture, which of the following is NOT a function of the Security Management Server (Security Management Server)?
- A. Display policies and logs on the administrator's workstation.
- B. Verify and compile Security Policies.
- C. Processing and sending alerts such as SNMP traps and email notifications.
- D. Store firewall logs to hard drive storage.
Answer: A
NEW QUESTION 17
An internal router is sending UDP keep-alive packets that are being encapsulated with GRE and sent through your R77 Security Gateway to a partner site. A rule for GRE traffic is configured for ACCEPT/LOG. Although the keep-alive packets are being sent every minute, a search through the SmartView Tracker logs for GRE traffic only shows one entry for the whole day (early in the morning after a Policy install).
Your partner site indicates they are successfully receiving the GRE encapsulated keep-alive packets on the 1-minute interval.
If GRE encapsulation is turned off on the router, SmartView Tracker shows a log entry for the UDP keep-alive packet every minute.
Which of the following is the BEST Explanation: for this behavior?
- A. The setting Log does not capture this level of detail for GR
- B. Set the rule tracking action to Audit since certain types of traffic can only be tracked this way.
- C. The log unification process is using a LUUID (Log Unification Unique Identification) that has become corrup
- D. Because it is encrypted, the R77 Security Gateway cannot distinguish between GRE session
- E. This is a known issue with GR
- F. Use IPSEC instead of the non-standard GRE protocol for encapsulation.
- G. The Log Server log unification process unifies all log entries from the Security Gateway on a specific connection into only one log entry in the SmartView Tracke
- H. GRE traffic has a 10 minute session timeout, thus each keep-alive packet is considered part of the original logged connection at the beginning of the day.
- I. The Log Server is failing to log GRE traffic properly because it is VPN traffi
- J. Disable all VPN configuration to the partner site to enable proper logging.
Answer: C
NEW QUESTION 18
Which command is used to obtain the configuration lock in Gaia?
- A. Lock database override
- B. Unlock database override
- C. Unlock database lock
- D. Lock database user
Answer: A
Explanation:
Obtaining a Configuration Lock
lock database override
unlock database
NEW QUESTION 19
Which of the following describes how Threat Extraction functions?
- A. Detect threats and provides a detailed report of discovered threats
- B. Proactively detects threats
- C. Delivers file with original content
- D. Delivers PDF versions of original files with active content removed
Answer: B
NEW QUESTION 20
Message digests use which of the following?
- A. DES and RC4
- B. IDEA and RC4
- C. SSL and MD4
- D. SHA-1 and MD5
Answer: D
NEW QUESTION 21
Fill in the blank: Authentication rules are defined for ____ .
- A. User groups
- B. Users using UserCheck
- C. Individual users
- D. All users in the database
Answer: A
NEW QUESTION 22
Fill in the blank: The IPS policy for pre-R80 gateways is installed during the _____.
- A. Firewall policy install
- B. Threat Prevention policy install
- C. Anti-bot policy install
- D. Access Control policy install
Answer: B
Explanation:
https://sc1.checkpoint.com/documents/R80/CP_R80BC_ThreatPrevention/html_frameset.htm?topic=documents
NEW QUESTION 23
Which directory holds the SmartLog index files by default?
- A. $SMARTLOGDIR/data
- B. $SMARTLOG/dir
- C. $FWDIR/smartlog
- D. $FWDIR/log
Answer: A
NEW QUESTION 24
......
Thanks for reading the newest 156-215.80 exam dumps! We recommend you to try the PREMIUM Dumpscollection.com 156-215.80 dumps in VCE and PDF here: https://www.dumpscollection.net/dumps/156-215.80/ (485 Q&As Dumps)
- Top Tips Of Most Recent 156-215.80 Free Dumps
- How Many Questions Of 156-315.80 Pdf Exam
- The Secret Of Check-Point 156-315.80 Exam
- Renew Check Point Certified Security Expert - R80 156-315.80 Pdf Exam
- Update 156-315.80 Free Question For Check Point Certified Security Expert - R80 Certification
- A Review Of Approved 156-315.80 Dumps
- What Refined 156-315.80 Test Questions Is
- All About Highest Quality 156-315.80 Actual Test

