156-315.80 Exam Questions - Online Test
156-315.80 Premium VCE File

150 Lectures, 20 Hours

It is impossible to pass Check-Point 156-315.80 exam without any help in the short term. Come to Examcollection soon and find the most advanced, correct and guaranteed Check-Point 156-315.80 practice questions. You will get a surprising result by our Improve Check Point Certified Security Expert - R80 practice guides.
Also have 156-315.80 free dumps questions for you:
NEW QUESTION 1
You find one of your cluster gateways showing “Down” when you run the “cphaprob stat” command. You then run the “clusterXL_admin up” on the down member but unfortunately the member continues to show down. What command do you run to determine the cause?
- A. cphaprob –f register
- B. cphaprob –d –s report
- C. cpstat –f all
- D. cphaprob –a list
Answer: D
NEW QUESTION 2
In the Check Point Security Management Architecture, which component(s) can store logs?
- A. SmartConsole
- B. Security Management Server and Security Gateway
- C. Security Management Server
- D. SmartConsole and Security Management Server
Answer: B
NEW QUESTION 3
What kind of information would you expect to see using the sim affinity command?
- A. The VMACs used in a Security Gateway cluster
- B. The involved firewall kernel modules in inbound and outbound packet chain
- C. Overview over SecureXL templated connections
- D. Network interfaces and core distribution used for CoreXL
Answer: D
NEW QUESTION 4
View the rule below. What does the lock-symbol in the left column mean? (Choose the BEST answer.)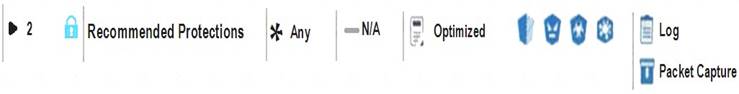
- A. The current administrator has read-only permissions to Threat Prevention Policy.
- B. Another user has locked the rule for editing.
- C. Configuration lock is presen
- D. Click the lock symbol to gain read-write access.
- E. The current administrator is logged in as read-only because someone else is editing the policy.
Answer: B
Explanation:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_
NEW QUESTION 5
You work as a security administrator for a large company. CSO of your company has attended a security conference where he has learnt how hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. He wants to make sure that his company has the tight protections in place. Check Point has been selected for the security vendor.
Which Check Point product protects BEST against malware and zero-day attacks while ensuring quick delivery of safe content to your users?
- A. IPS AND Application Control
- B. IPS, anti-virus and anti-bot
- C. IPS, anti-virus and e-mail security
- D. SandBlast
Answer: D
NEW QUESTION 6
What is the recommended number of physical network interfaces in a Mobile Access cluster deployment?
- A. 4 Interfaces – an interface leading to the organization, a second interface leading to the internet, a third interface for synchronization, a fourth interface leading to the Security Management Server.
- B. 3 Interfaces – an interface leading to the organization, a second interface leading to the Internet, a third interface for synchronization.
- C. 1 Interface – an interface leading to the organization and the Internet, and configure for synchronization.
- D. 2 Interfaces – a data interface leading to the organization and the Internet, a second interface for synchronization.
Answer: B
NEW QUESTION 7
Which blades and or features are not supported in R80?
- A. SmartEvent Maps
- B. SmartEvent
- C. Identity Awareness
- D. SmartConsole Toolbars
Answer: A
NEW QUESTION 8
Which of the following Windows Security Events will not map a username to an IP address in Identity Awareness?
- A. Kerberos Ticket Renewed
- B. Kerberos Ticket Requested
- C. Account Logon
- D. Kerberos Ticket Timed Out
Answer: D
NEW QUESTION 9
In the R80 SmartConsole, on which tab are Permissions and Administrators defined?
- A. Security Policies
- B. Logs and Monitor
- C. Manage and Settings
- D. Gateways and Servers
Answer: C
NEW QUESTION 10
Which of the following type of authentication on Mobile Access can NOT be used as the first authentication method?
- A. Dynamic ID
- B. RADIUS
- C. Username and Password
- D. Certificate
Answer: A
NEW QUESTION 11
When a packet arrives at the gateway, the gateway checks it against the rules in the hop Policy Layer, sequentially from top to bottom, and enforces the first rule that matches a packet. Which of the following statements about the order of rule enforcement is true?
- A. If the Action is Accept, the gateway allows the packet to pass through the gateway.
- B. If the Action is Drop, the gateway continues to check rules in the next Policy Layer down.
- C. If the Action is Accept, the gateway continues to check rules in the next Policy Layer down.
- D. If the Action is Drop, the gateway applies the Implicit Clean-up Rule for that Policy Layer.
Answer: C
NEW QUESTION 12
For best practices, what is the recommended time for automatic unlocking of locked admin accounts?
- A. 20 minutes
- B. 15 minutes
- C. Admin account cannot be unlocked automatically
- D. 30 minutes at least
Answer: D
NEW QUESTION 13
Which utility allows you to configure the DHCP service on Gaia from the command line?
- A. ifconfig
- B. dhcp_ofg
- C. sysconfig
- D. cpconfig
Answer: C
NEW QUESTION 14
Joey wants to upgrade from R75.40 to R80 version of Security management. He will use Advanced Upgrade with Database Migration method to achieve this.
What is one of the requirements for his success?
- A. Size of the /var/log folder of the source machine must be at least 25% of the size of the /var/log directory on the target machine
- B. Size of the /var/log folder of the target machine must be at least 25% of the size of the /var/log directory on the source machine
- C. Size of the $FWDIR/log folder of the target machine must be at least 30% of the size of the$FWDIR/log directory on the source machine
- D. Size of the /var/log folder of the target machine must be at least 25GB or more
Answer: B
NEW QUESTION 15
Which view is NOT a valid CPVIEW view?
- A. IDA
- B. RAD
- C. PDP
- D. VPN
Answer: C
NEW QUESTION 16
To fully enable Dynamic Dispatcher on a Security Gateway:
- A. run fw ctl multik set_mode 9 in Expert mode and then Reboot.
- B. Using cpconfig, update the Dynamic Dispatcher value to “full” under the CoreXL menu.
- C. Edit/proc/interrupts to include multik set_mode 1 at the bottom of the file, save, and reboot.
- D. run fw multik set_mode 1 in Expert mode and then reboot.
Answer: A
NEW QUESTION 17
......
Recommend!! Get the Full 156-315.80 dumps in VCE and PDF From Allfreedumps.com, Welcome to Download: https://www.allfreedumps.com/156-315.80-dumps.html (New 428 Q&As Version)
- A Review Of Approved 156-315.80 Dumps
- All About Highest Quality 156-315.80 Actual Test
- Renew Check Point Certified Security Expert - R80 156-315.80 Pdf Exam
- The Secret Of Check-Point 156-315.80 Exam
- What Refined 156-315.80 Test Questions Is
- How Many Questions Of 156-315.80 Pdf Exam
- Top Tips Of Most Recent 156-215.80 Free Dumps
- Update 156-315.80 Free Question For Check Point Certified Security Expert - R80 Certification

